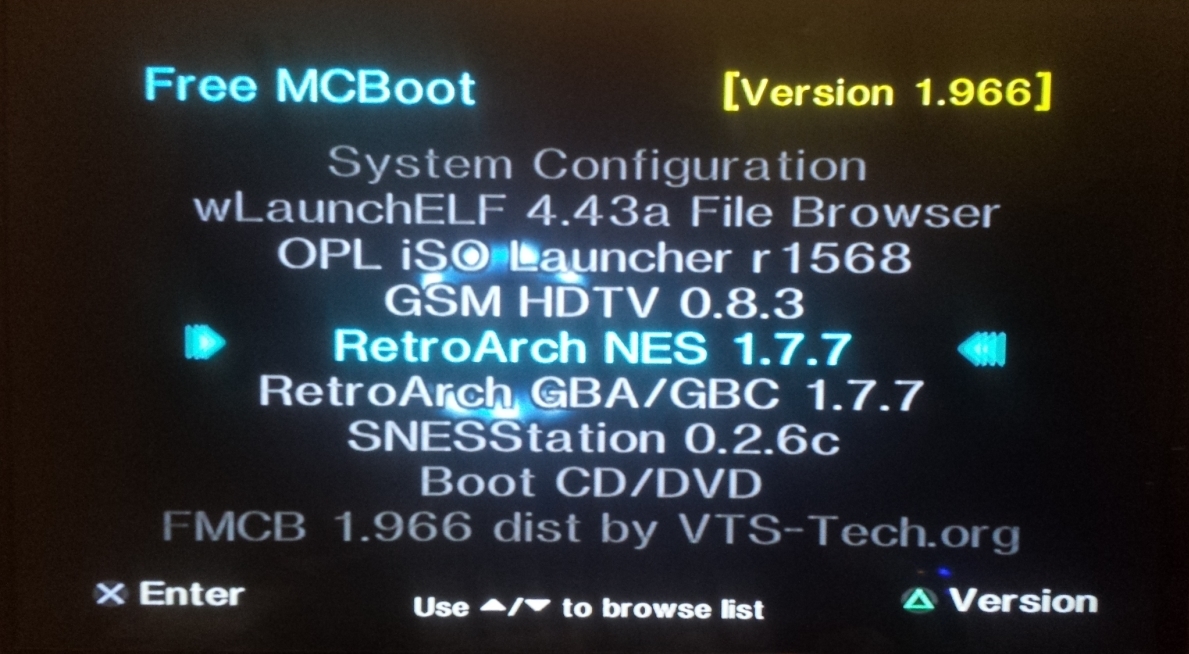
Burnout Revenge SLUS-21242 No DNAS + No Encryption
Destruction Derby Arenas SLUS-20855 No DNAS
FIFA 06 SLUS-21280 No DNAS + No Encryption (Patch ISO Mode 3)
Fight Night Round 2 SLUS-21161 No DNAS
Madden NFL 05 SLUS-21000 No DNAS
NASCAR 08 SLUS-21639 No DNAS + No Encryption
NASCAR 09 SLUS-21744 No DNAS + No Encryption
NASCAR Thunder 2004 SLUS-20824 No DNAS
NBA Street V3 SLUS-21126 No DNAS + No Encryption
NHL 07 SLUS-21458 No DNAS
Network Adapter Startup Disc 2.5 SCUS-97356 No DNAS (Rename)
Online Startup Disc 3.0 PBPX-95239 No DNAS (Rename)
Online Startup Disc 3.5 PBPX-95247 No DNAS (Rename)
Online Startup Disc 4.0 PBPX-95248 No DNAS
Online Startup Disc 4.0 SCUS-97357 No DNAS
SSX3 SLUS-20772 No DNAS
Test Drive Unlimited SLUS-29192 No DNAS (Prototype)
Test Drive Unlimited SLUS-21490 No DNAS
Category: Blog
Buy Direct from VTSTech
Save money by buying direct from me. $1-5 off list price on eBay for most items.
These are the products I regularly have for sale all the time.
To start your order Use my VTSTech Shop, Bonanza or simply E-mail [email protected] with “ORDER” in the subject line and I’ll respond shortly. Provide Mailing Address for Shipping Estimates. PayPal & BitCoin accepted. All prices in Canadian Dollars.
Tracking Numbers provided after Transaction ID received. All items fully insured for damage during shipping. Free E-Mail support with all purchases.
Shipping available to Canada, USA and Europe
(Small items can ship without tracking for $1 via Canada Post Lettermail. With tracking about $10, $30-50 for heavier items like Complete Console bundles.)
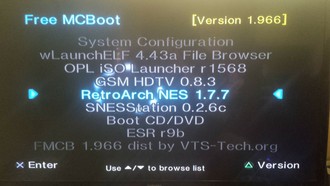

Sony PS2 8MB FMCB Free MC Boot Memory Cards
Only $14.99 CAD (Reg $15.99-17.99 on eBay)

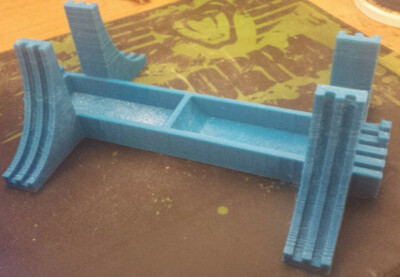
Sony PlayStation 2 PS2 Slim Vertical Stand – SCPH-90110 Remix – 3D Printed
Only $8.99 CAD (Reg $9.99 on eBay)

Sony PlayStation Controller Stand – Hanging Desk Mount 3D Printed by VTSTech
Only $8.99 CAD (Reg $9.99 on eBay)


Sony PlayStation 3 PS3 Slim Vertical Stand – 3D Printed
Only $8.99 CAD (Reg $9.99 on eBay)


Sony PlayStation 3 PS3 Super Slim HDD Tray/Mount/Bracket – 3D Printed CECH-4XXX
Only $3.99 CAD (Reg $4.99 on eBay)
PlayStation Console Stands & Controller Stands – #3DPrinted
PS2 Memory Cards pre-installed with FMCB 1.966
PS3/Slim/Super Slim Model Identification
Top to Bottom: Super Slim, Slim, Original

Original
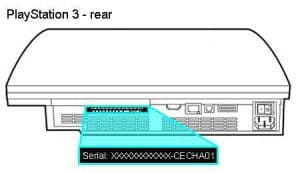
Slim
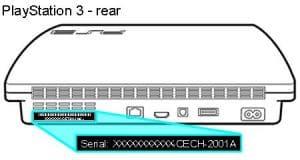
Super Slim

PS2/PS2 Slim Model Identification
Model # Location


PS1/PSOne Model Identification
The 2017 Guide to creating a BitCoin wallet and making BitCoin.

Welcome to The 2017 Guide to getting a BitCoin wallet & making BitCoin (BTC)
This will be a 3 part guide. This is part 1.
First off, If you do not already have a BitCoin Address, or BitCoin Wallet. You have a few options.
Quick & Easy Online Wallet.
More Advanced Application Based Wallet
MultiBit
I prefer MultiBit Classic. The folks at MultiBit have written a handy ‘Installation‘ as well as ‘Creating a Wallet‘ Guide for MultiBit Classic.
multibit-classic-windows-0.5.19.exe (x86)
multibit-classic-windows-x64-0.5.19.exe (x64)
You may prefer MultiBit HD. They have also written a ‘Installation‘ and ‘Creating a Wallet‘ Guide for MultiBit HD.
multibit-windows-0.4.1.exe (x86)
multibit-windows-x64-0.4.1.exe (x64)
Next you need to find a faucet payment provider/processor. This is free and anonymous. I used FaucetHub.io. All of the faucets I list here will use FaucetHub.io
I will organize this list over the coming days as well as add more links. But this is more than enough to get you started.
Check back for Part 2. BitCoin Games & BitCoin Gambling.
Part 3 will cover Mining, Cloud Mining and Escrow
What is a Vulnerability Assessment?
A vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Examples of systems for which vulnerability assessments are performed include, but are not limited to, information technology systems, energy supply systems, water supply systems, transportation systems, and communication systems. Such assessments may be conducted on behalf of a range of different organizations, from small businesses up to large regional infrastructures. Vulnerability from the perspective of disaster management means assessing the threats from potential hazards to the population and to infrastructure. It may be conducted in the political, social, economic or environmental fields.
Source: Wikipedia
What is Penetration Testing?
A penetration test, informally pen test, is an attack on a computer system that looks for security weaknesses, potentially gaining access to the computer’s features and data.[1][2]
The process typically identifies the target systems and a particular goal—then reviews available information and undertakes various means to attain the goal. A penetration test target may be a white box (which provides background and system information) or black box (which provides only basic or no information except the company name). A penetration test can help determine whether a system is vulnerable to attack, if the defenses were sufficient, and which defenses (if any) the test defeated.[3]
..
Penetration tests are a component of a full security audit. For example, the Payment Card Industry Data Security Standard requires penetration testing on a regular schedule, and after system changes.[6]
Source: Wikipedia